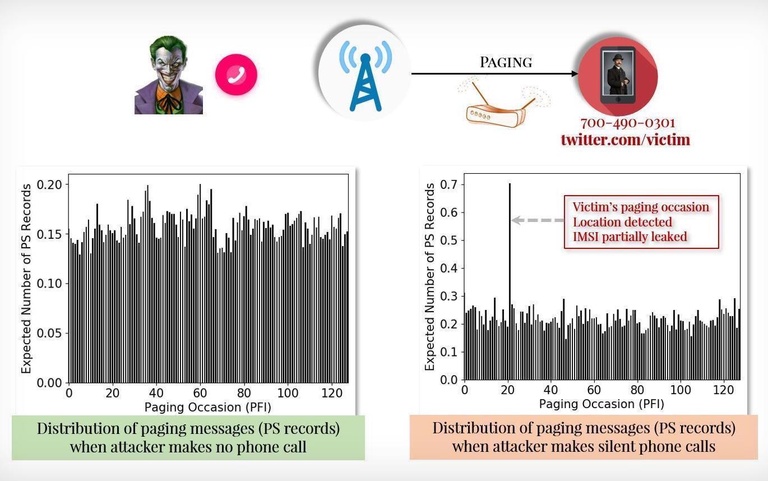
"The paper [... ] details the attacks: the first is ToRPEDO, which exploits a weakness in the paging protocol that carriers use to notify a phone before a call or text message comes through. The researchers found that several phone calls placed and cancelled in a short period can trigger a paging message without alerting the target device to an incoming call, which an attacker can use to track a victim’s location. Knowing the victim’s paging occasion also lets an attacker hijack the paging channel and inject or deny paging messages, by spoofing messages like as Amber alerts or blocking messages altogether, the researchers say. [...]
Hussain, along with Ninghui Li and Elisa Bertino at Purdue University, and Mitziu Echeverria and Omar Chowdhury at the University of Iowa are set to reveal their findings at the Network and Distributed System Security Symposium in San Diego on Tuesday."
More at:
- https://relentless-warrior.github.io/files/paging-ndss19-preprint.pdf
- Torpedo 4G attack locates social media users [paywall]: "The identification of new vulnerabilities in 4G networks has paved the way for a more economical way to monitor targets using their digital identity."
- Holes in 4G and 5G Networks Could Let Hackers Track Your Location (Wired)
- Purdue News Release
- UI College of Liberal Arts and Sciences News Release
At NDSS 2019, Chowdhury will also be presenting, with student Daniel Yahyazadeh et al.: Analyzing Semantic Correctness with Symbolic Execution: A Case Study on PKCS#1 v1.5 Signature Verification